Staff Dishonesty in the Retail Sector
Understanding the role of opportunity
Table of Contents:
- Abstract
- Executive Summary
- - Key Findings
- - Recommendations
- Introduction
- Background to Staff Dishonesty
- - Defining Staff Dishonesty
- - Scale and Extent of the Problem
- - Explaining Staff Dishonesty
- Methodology
- - Interviews with Offenders
- - Analysis of Existing Records
- Interviews with Selected Security Staff
- Questionnaires Completed by Security Staff
- Limitations
- The Data Set
- Type of staff
- Key Findings
- - Place of Offending
- - Methods of Offending
- The Role of Process Failures and Offending
- Offending and Prevention
- Conclusions
- Recommendations
- - Developing a Data Mining Capability at the Till
- - Staff Monitoring and Surveillance
- - Regular Reviews of Key Vulnerable Processes
- - Hot Product Reviews
- - Staff Awareness Programmes
- - Management Performance Reviews
- - Developing a Culture of Intolerance
Languages :
This report, which was published in 2003, presents results from a study focused upon developing a better understanding of the factors that make particular stores within a retail estate more vulnerable to shrinkage – the ‘hot store’ phenomena.
The study is based upon a survey of retailers and a series of retailer case studies, including visits to retail stores, and interviews with key personnel in four companies.
The study concludes that the role of the store management team seems extremely important in explaining the difference between high and low performing stores – evidence highlighted key differences in the style and approach adopted, the importance of longevity of service and the need to build staff morale and confidence.
Four key areas were identified in low shrinkage stores: Accountability, Attitude, Action and Audit. Better performing stores had managers who took accountability for the issue of shrinkage. They recognised it as a critical part of their job and prioritised it accordingly. Similarly, good stores had managers whose attitude was focused on developing their staff and seeing them as key members of the team – they were keen to work with their staff to improve their skills and generate positive staff morale. Moreover, low shrinkage stores were characterised by a strong adherence to procedures – managers took action to make sure that staff constantly complied with them and took pride in the appearance of all parts of the store. Lastly, managers in better performing stores recognised the need to constantly monitor and measure the problem of shrinkage – they prioritised the role of audit and used data to help them develop shrinkage reduction strategies appropriate to their context.
The report also found that environmental factors cannot be excluded from the equation as well. The nature of the store itself was found to play a role in explaining some of the differences between good and bad stores and areas with high levels of social deprivation, particularly high crime rates are likely to attract more customers and staff likely to steal. However, the study found no evidence which showed a statistical link between levels of shoplifting and rates of shrinkage, although there was some evidence that rates of staff dismissal and shoplifting were associated.
The overall conclusion from this study is that the way in which a store is managed is the key factor in explaining why some stores have higher rates of loss than others. While the environment within which the store is located does play a role, good management teams recognise this and develop strategies accordingly to meet the challenge they face.
Abstract
This report, which was published in 2003, presents results from a study focused upon developing a better understanding of the factors that make particular stores within a retail estate more vulnerable to shrinkage – the ‘hot store’ phenomena.
The study is based upon a survey of retailers and a series of retailer case studies, including visits to retail stores, and interviews with key personnel in four companies.
The study concludes that the role of the store management team seems extremely important in explaining the difference between high and low performing stores – evidence highlighted key differences in the style and approach adopted, the importance of longevity of service and the need to build staff morale and confidence.
Four key areas were identified in low shrinkage stores: Accountability, Attitude, Action and Audit. Better performing stores had managers who took accountability for the issue of shrinkage. They recognised it as a critical part of their job and prioritised it accordingly. Similarly, good stores had managers whose attitude was focused on developing their staff and seeing them as key members of the team – they were keen to work with their staff to improve their skills and generate positive staff morale. Moreover, low shrinkage stores were characterised by a strong adherence to procedures – managers took action to make sure that staff constantly complied with them and took pride in the appearance of all parts of the store. Lastly, managers in better performing stores recognised the need to constantly monitor and measure the problem of shrinkage – they prioritised the role of audit and used data to help them develop shrinkage reduction strategies appropriate to their context.
The report also found that environmental factors cannot be excluded from the equation as well. The nature of the store itself was found to play a role in explaining some of the differences between good and bad stores and areas with high levels of social deprivation, particularly high crime rates are likely to attract more customers and staff likely to steal. However, the study found no evidence which showed a statistical link between levels of shoplifting and rates of shrinkage, although there was some evidence that rates of staff dismissal and shoplifting were associated.
The overall conclusion from this study is that the way in which a store is managed is the key factor in explaining why some stores have higher rates of loss than others. While the environment within which the store is located does play a role, good management teams recognise this and develop strategies accordingly to meet the challenge they face.
Executive Summary
The purpose of this project was to develop greater understanding of the ways in which dishonest members of staff exploited retail processes and procedures to steal cash and goods from their employers. It is based upon data collected directly from offenders themselves together with interviews with loss prevention staff responsible for deterring and detecting such behaviour. As such it sought to make a valuable contribution in an area that has to date been little understood and researched.
The data is derived from four retail companies based upon direct interviews with offenders, analysis of taped interviews between security staff and those suspected of being dishonest, questionnaires completed by security staff interviewing staff receiving their ‘exit’ interview, and interviews with a select group of security practitioners. In total, some 74 cases generated data on 99 ‘dishonest’ events occurring primarily in retail stores (two offenders were interviewed who had colluded to steal stock from a retail distribution centre).
Key Findings
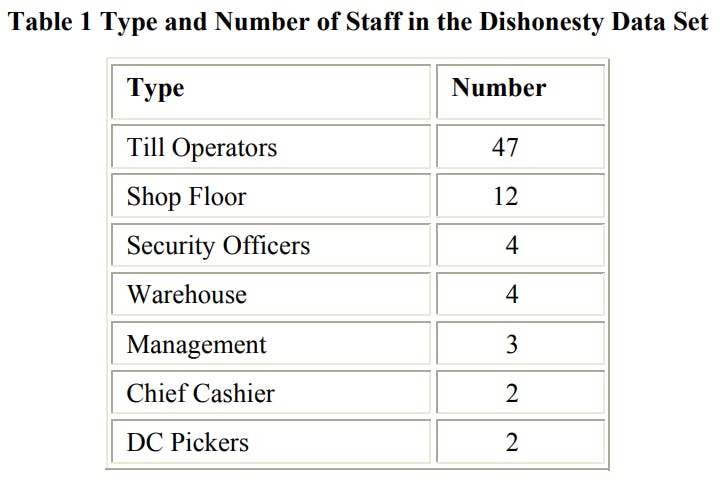
Of the 74 cases, 47 were till operators, with a further 12 working primarily on the shop floor. The rest were security officers, store management staff, cashiers, warehouse staff and distribution centre pickers.
The vast majority of offending took place at the till (69% of incidents) followed by the back-ofstore (16%). Very few incidents took place on the shop floor, at the refund counter or in the cash office.
The most frequent method of offending at the till was to take cash, followed by the non-scanning of items for family, friends and colleagues, allowing friends and family to use a staff member’s discount card, adding points to their own loyalty card and serving family and friends. Relatively few made any effort to conceal their tracks through manipulation of the till (last item voids, offering discounts, deliberately short changing customers etc).
The most frequent method of offending in the back-of store was to eat stock, take items out of the back of the store (either walk out with them or hide them in the garbage area) or simply secrete goods about their person and leave the store as normal.
The research identified a number of vulnerable processes and procedures:
- Security searches were either not random or simply not done.
- Staff sharing till pin numbers or not logging off at the end of shifts.
- Tills not being emptied and checked on a regular basis.
- Staff not leaving by staff exits.
- Irregularities in use of the security cage.
- Unauthorised staff entering the warehouse
- Lack of supervision of night shift workers.
In terms of prevention and detection, respondents suggested:
- CCTV as an effective means of reducing offending at the till (because it provided an evidential link between a till discrepancy and themselves).
- Staff searches that were genuinely random and covered all types of staff.
- Better training for staff on the data mining and exception reporting capability of store systems to change their misconceived notions about the unlikeliness of being detected.
- Greater checking on till compliance.
- Better screening of applicants to reduce the number of previous staff thieves joining the company.
- Increased staff awareness of the implications of breaching company procedures such as serving family and friends or letting them use a discount card.
- An increase in the number checks and patrols carried out by store security staff and management.
Recommendations
A number of recommendations are proposed:
- Developing a data mining capability at the till to increase detection rates.
- Increasing the extent of staff monitoring and surveillance primarily through the use of CCTV, staff searches, greater supervision of staff working at night, reducing the degree of discretion staff have at the till through checks and supervisory oversight.
- Carrying out regular reviews of key vulnerable store processes to identify poor adherence and compliance.
- Carrying out regular reviews of hot products targeted by staff to ensure focus is maintained and new trends in offending are identified.
- Improving staff awareness programmes to highlight the data mining and exception reporting capability of the business, the scope of CCTV coverage in the store, and the implications of being caught offending.
- Ensuring that management performance reviews are regularly undertaken to remind management staff of their role-model responsibilities within the store environment.
- Developing a culture of integrity within the store whereby staff are less likely to tolerate working with staff who are behaving dishonestly
Introduction
Whilst rarely being at the top of the agenda, getting to grips with the issue of employee dishonesty has been a perennial concern for loss prevention practitioners. It is one of those issues that is constantly perceived to be a significant threat to business integrity and yet relatively little seems to be done about it. This is partly because most organisations are prone to sweep it under the carpet as something far too sensitive to address, or prefer to focus their energies on external threats which are viewed to be more palatable to corporate tastes and certainly less embarrassing when discussed in the public arena. Academic research on the problem has been undertaken over many decades starting with Sutherland’s pioneering work on white collar crime back in the 1930s and 1940s1 . However, much of this work has been focussed on defining the problem and understanding why offenders commit this type of behaviour – the search for the ‘who’, ‘what’ and the ‘why’ has been extensively studied and understood. What is much less clear is the ‘how’. How do dishonest employees go about stealing from the organisations that employ them? What are the techniques and tricks that they use? How do they avoid and overcome the organisational processes and procedures put in place to deter and detect such behaviour? In what ways do they manipulate loopholes within business operations to enable them or their family and friends to steal stock and cash? These are questions that are much more difficult to answer but potentially are extraordinarily important to organisations interested in trying to deal with this problem.
Some research has been done on this issue but most studies have a fundamentally flawed methodology – they tend to base their research upon the views of staff currently working within organisations – asking them whether they would be likely to steal and if they would, what they would steal, how and where they would do it. Crucial questions, but being answered by the wrong audience. Asking staff in general about how to steal from their company is useful but essentially flawed as they will probably be guessing or using their imagination to decide how an offender might act. Who will definitely know are those that have been caught for the offence and disciplined, dismissed or prosecuted by the company or the criminal justice system. These are the people who are best ‘qualified’ to answer these questions and offer genuine information on how to commit staff dishonesty in the workplace. The problem is that this is potentially a very difficult group to garner information from – they are often difficult to identify and contact, and incentivising them to discuss their previous behaviour can be extremely challenging. Yet studies in other areas of criminal justice have successfully adopted this approach and added considerably to our understanding, particularly in terms of crime prevention2 .
Getting answers to the ‘how’ question was the purpose of this research study. It aimed to gather information from as many sources as possible, including those who have been previously caught offending, about how dishonest staff steal from their organisations. The study had three objectives:
- Gather real insights into how workers in the supply chain exploit company procedures and processes to steal cash and goods.
- Understand offender perspectives on current shrinkage management strategies in order to understand what currently works, what does not and what might work in the future.
- Provide a greater appreciation of the nuances of ‘sweet-hearting’ at the till and understand how operators do it, how they make sure they are not caught, and the types of till procedures that facilitate or inhibit this activity.
The study used a number of complementary data collection methodologies: direct interviews with offenders themselves, interviews with security staff responsible for deterring and detecting employee theft, analysis of taped interviews with offenders, and questionnaires completed by security staff interviewing employees suspected of dishonesty. This is the first time such an approach has been adopted to try and fully understand how staff actually steal from retail organisations. The report is structured into four sections. The first part offers some background on the nature of the problem of staff dishonesty and reviews what is currently known about it from existing research. The second section explains in detail the methodology used to carry out this study, while section three presents the findings. The final section offers a conclusion, summary and key recommendations.
Background to Staff Dishonesty
This section of the report provides an overview of the current thinking on the problem of staff dishonesty, and summarises an extensive review of the current academic literature on the subject. In particular, it looks at current definitions, the scale and extent of the problem, and the available explanations for why staff engage in dishonest behaviour in the work place.
Defining Staff Dishonesty
There are a number of definitions of employee theft, ranging from the very broad such as Gruys and Sackett’s: ‘any intentional behaviour on the part of an organisational member viewed by the organisation as contrary to its legitimate interests’3 , to the more specific such as that developed by Hollinger and Clark: ‘the unauthorised taking, control or transfer of money and/or property of the formal work organisation perpetrated by an employee during the course of occupational activity which is related to his or her employment4 . It is this second definition that will be primarily used for the purpose of this report although some breaches of company policy will be included that may not necessarily have been apart of the Hollinger and Clarke thinking. These include the serving of friends and family and the misuse of loyalty schemes and staff discount cards.
Hollinger and Clark’s work also made an important distinction between property deviance and production deviance, the former being the theft of, or deliberate damage to, company assets, while the latter refers to counterproductive behaviour within the workplace, such as the ‘stealing of time’, absenteeism, not completing tasks properly, and general tardiness5 . This research is primarily going to focus on property deviance.
Scale and Extent of the Problem
Deciding upon the rate of incidence (number of times a theft occurs) and prevalence (number of staff involved) of dishonesty has been an elusive challenge for researchers interested in this subject. This is caused primarily by a lack of data, both official, such as police statistics, and company specific, such as human resource files. Most incidents of staff dishonesty that are discovered by an organisation rarely end up in the official criminal statistics. This is because most companies prefer to deal with the problem internally either through dismissal, demotion or other disciplinary action. Indeed, the rationale for such an approach is usually to avoid any adverse publicity or attract attention to internal weaknesses within the company. However, a number of self report studies have been carried out around the world that have attempted to estimate the extent to which staff dishonesty is accountable for organisational losses within the retail sector.
For instance, the annual studies undertaken by the University of Florida, which began in 1991, estimate that internal theft is responsible for between 40 and 47 per cent of all losses6 . The two sweeps of the ECR Europe shrinkage survey in 2000 and 2004, which suggested that staff theft accounted for 24 and 28 per cent respectively7 , and the Retail Theft Barometer, which found that its sample of retailers thought that 28 per cent of loss was due to internal theft8 . Of course, all of these studies suffer from the same fundamental flaw, which is that the responses are simply based upon the ‘informed’ guesses of the respondents rather than on any hard evidence. Most retailers taking part in these self report studies suffer from the same problem, which is that most of their losses are unknown to them. For instance, the 2004 ECR Shrinkage Survey found that retailers estimated that 51 per cent of their losses were unknown9 . This means that any estimates of the extent to which staff dishonesty is accountable for losses are riddled with uncertainty. Undoubtedly, retailers on the whole find it much more palatable to apportion these unknown losses to external rather than internal threats – better to blame those outside the organisation than those who are blatantly abusing the trust of their employer or taking advantage of their position.
Looking more broadly, research suggests that employee theft in the US costs businesses billions of dollars each year. One study estimated that a typical organisation loses 6 per cent of its annual revenue due to staff dishonesty, which in the US equates to $660 billion per annum10. Another estimated that 30 per cent of all small business failures were caused by employee dishonesty11. Ultimately though, it is the consumer who must meet the cost of staff dishonesty through the increased cost of goods in the stores12.
Explaining Staff Dishonesty
Understanding why some staff steal from organisations is a complex issue, as different types of staff (levels of responsibility and specialisation) in different circumstances (work-based and nonwork based) require different explanations for their offending behaviour. However, studies have identified a number of key explanations.
- First, some studies have suggested that staff who are under external financial pressures, such as high levels of personal debt may be inclined to steal from their employers to ease their financial burden13. Others however, have disputed this explanation and have suggested that it plays only a minor role in explaining deviant behaviour amongst employees14. More recently, the overall rise in consumer debt over the past 10 years has once again raised this as a key issue in explaining staff dishonesty although no recent empirical studies are available to shed light on this15.
- Secondly, studies have shown that opportunity is the key to understanding why some staff engage in deviant behaviour16, indeed more generalised criminological theories have been developed that clearly elaborate the link between available opportunity and dishonest behaviour17. This work has explored how successful crime prevention is based upon reducing the opportunity for offenders to commit crime, usually through target hardening, benefit denial and increased surveillance. Certainly when you consider the average retail environment, staff are often surrounded by opportunities, particularly more senior staff or those working anti-social hours such as shelf stackers or cleaners, or those with minimal amounts of supervision such as those staff responsible for small outlets where they may be working on their own
- Thirdly, job dissatisfaction can be an explaining variable for some acts of staff dishonesty. Staff who are unhappy with their working environment or circumstances have been shown to be much more likely to offend18. This could be related to a number of factors including their attitude towards their work environment, their relationship with line management or levels of staffing. Members of staff who feel dissatisfied are more likely to explain their deviant behaviour as a means to get back at an employer who is considered to be treating them unfairly or badly.
- Fourthly, and linked to the previous point, some staff may steal because they feel they are not paid what they would consider a sufficient wage, or they perceive inequities in remuneration packages within the organisation19. This can lead to staff perceiving that they are being ‘ripped off’ by the company and hence they are justified in taking cash or goods to compensate for their ‘poor’ treatment.
- Fifthly, the role of company culture has been identified as a possible factor in explaining why some staff steal from their employers20. For instance, if staff see their line managers taking stock or eating produce, then they are likely to perceive that they too can indulge in this behaviour. Similarly, if the organisation is permeated with an attitude that tolerates deviant behaviour or uses a vocabulary that makes it more morally ambiguous (‘borrowing’ things from the workplace) then this can have a major effect upon staff attitudes to theft.
- Sixthly, research has been done looking at how the attitude of staff varies depending upon their age and status within the organisation. For instance, Speed looked at the offending behaviour of young, part time and temporary staff and compared that with more senior staff within the company21. He established that different preventative strategies need to be used depending on these factors.
- Finally, research has been undertaken looking at how staff neutralise their feelings of guilt concerning dishonest behaviour. Some staff are able to rationalise their offending as morally acceptable – the company can afford it, or it is perceived as a victimless crime22. This process of ‘neutralisation’ has been found to be highly correlated with staff who are more likely to steal23.
As can be seen, there is a considerable amount of research that has been undertaken in the past 50 years or so trying to understand the phenomenon of staff dishonesty. What can be concluded is that it is something that is undoubtedly very hard to measure, and current estimates tell us more about the attitudes of those providing the data than the real extent of the problem. It is also clear that staff who are unhappy in their workplace, feel marginalised and insufficiently rewarded are much more likely to engage in deviant behaviour. Moreover, many dishonest staff are able to neutralise their offending through either not perceiving it as a crime in the first place (there is no obvious victim), feeling that they are owed something by the company (I am not properly rewarded), or viewing it is an accepted part of the organisational culture (everybody does it).
Methodology
A review of the existing literature on staff dishonesty reveals that no previous studies have been undertaken that have spoken directly with offenders to find out their mindset, motivation, modus operandi and attitude towards security measures. And yet, gaining insights from offenders is now an established and well-regarded methodological approach. It enables the researcher to find out directly how an offence was committed and why. The offender can be questioned in detail as to the methods they adopted, their knowledge of the systems in place at the time of the offence and the means by which they were eventually caught. However, gaining access to staff who have been found ‘guilty’ of stealing from the organisation that previously employed them is not easy. Few end up going through the formal criminal justice channels and hardly any are sent to prison (a place where offender-based research is often carried out). Given this problem, the project adopted a multi-stream approach to data collection to ensure that if interviews with offenders were not possible, other mechanisms were in place that would enable the project’s overall aims and objectives to be met. This method would also allow for a degree of triangulation of data sources which would further increase the veracity of any subsequent findings. The data collections methods were as follows:
- Interviews with known offenders.
- Analysis of existing records held by companies on staff dismissed for dishonesty.
- Interviews with selected security staff who have responsibility for deterring and detecting offenders.
- Questionnaires completed by security staff who are interviewing suspected employees
Interviews with Offenders
Two companies agreed to take part, both of which wish to remain anonymous. Both were large UK retailers operating nationally and internationally offering a broad range of goods including clothing, electrical, food and alcohol. Because the Data Protection Act in the UK prohibits the sharing of personal information without the express permission of the data subject, the process of contacting staff who had been dismissed was complex. Each participating company agreed to send a letter to a list of staff dismissed for dishonesty in the last 12 months (In total, some 930 letters were sent out). This letter asked if they would give their permission for research staff to contact them to arrange an interview. Once positive replies were received, these were then passed on to the research team who duly arranged to contact the former member of staff to arrange a suitable interview time. A small incentive was offered to those agreeing to take part, which was a retail voucher to the value of £20. The interviews were carried out by staff working for Perpetuity Research and Consultancy International24.
It was very unclear how successful this approach would be, but by the end of the data collection phase, 35 interviews had been completed. Each interview was tape recorded and subsequently transcribed.
Analysis of Existing Records
A second data collection strategy was to try and find companies that kept records of incidents of staff dishonesty. Luckily, one the ECR Shrinkage Group members: Wilkinson’s, a UK retail company, tape records all their investigative interviews with staff suspected of dishonesty. A total of 15 interviews were provided and each was analysed and notes made on the issues relevant to this research. This proved to be a particularly rich source of data as the interviews often lasted longer than an hour and the interviewer was highly skilled in extracting a broad range of information from those confronted with accusations of dishonesty. The process of uncovering the circumstances and previous history of offending was especially useful from this data source.
Interviews with Selected Security Staff
In order to gather as broad a range of information as possible about how staff stole from retail organisations, it was decided to carry out interviews with a small number of security staff who had specialist knowledge of staff dishonesty. Interviews were carried out with 2 members of the Ahold retail organisation – they were selected because another of the data sources was provided by this company and the interviewees would be able to provide useful context for this data. The first was the Head of Security for Ahold in Poland. The interview took place in Warsaw in one of the company’s stores. A broad ranging interview schedule was used covering recent investigations into dishonest staff, the approaches adopted by them, the specific vulnerabilities of the till within Ahold stores, and methods adopted by the company to deter and detect staff. The second interview was with a senior member of the security team for the Albert Heijn retail brand. This interview took place in the Netherlands and the respondent was selected because of their experience in undertaking investigations into staff dishonesty (they were responsible for a team of investigators dedicated to this particular problem).
Questionnaires Completed by Security Staff
The final approach adopted was the completion of a short questionnaire designed for security staff to use when they were interviewing a member of staff who was strongly suspected of dishonesty (the ‘exit’ interview as it is often described). The questionnaire was inevitably short and to the point as it was felt unlikely that staff who were in the process of being dismissed would be positively inclined to answer a series of research questions. The investigative team at Albert Heijn in the Netherlands agreed to use the research instrument and over a 3 month period they completed 31 questionnaires. It should be noted that given the focus of the investigative team at Albert Heijn (cash losses), much of the data, but not all focused on cash-based rather than product-based offending. This needs to be taken into account when reviewing the overall findings from the entire data set.
Limitations
As with any research methodology, there are inevitable limitations and this research is no exception. Clearly when contacting offenders through the mechanisms described above, it is possible that a skewed sample is created – there may be something different about those that agreed to take part compared with those that refused to make contact. From the data available from the participating companies, no obvious indicators of this are visible (such as age, gender, position) but it is possible and this needs to be considered when reviewing the findings. As with all offender-based interview methodologies, there is a danger that you are only ever talking to those who are especially inept at dishonest behaviour (hence the reason why they were caught in the first place). They may therefore not be familiar with the techniques and approaches of those who are successful and never caught. Similarly, the group of people taking part, have to a certain extent a history of deviancy and so it is possible that they may be inclined to be less than truthful about their previous behaviour. However, other research with offenders has found that on the whole they are remarkable honest when describing their previous offending (they are slightly prone to embellishment but relatively little outright deceit)25. Once again this needs to be taken into account when reviewing the results from this research.
Overall, the methodology adopted, particularly in terms of using four different approaches to data collection gives this project a relatively high degree of robustness and validity and therefore the author has a high degree of confidence in the results presented in the following section.
The Data Set
From the three main sources of data on offending behaviour (direct interviews with offenders, analysis of taped interviews with suspected offenders, and questionnaires completed by security staff interviewing suspected staff), a total of 74 usable cases have been identified (those that pleaded their innocence and denied any wrongdoing whatsoever were excluded). These cases covered a large number of incidents – many hundreds of admitted incidents although as expected there were a small minority of offenders who accounted for the vast majority of claimed incidents (for instance one offender admitted to stealing several hundred times over a one year period). The sums admitted to also varied enormously, from as little as €0.55 to over €150,000. However, 99 ‘dishonest’ events have been captured as part of the analysis and they form the core of the findings section. In addition, some offenders offered their views on breaches in process failure and methods likely to have either deterred them or at least detected their behaviour earlier. These thoughts are also presented in the next section.
It is worth reflecting upon what is meant by a ‘dishonest’ event in this context. The data set is derived from four different companies, all of whom have different interpretations about what is deemed to be staff dishonesty. At one end of the spectrum they are all in agreement – the theft of stock and cash is universally agreed upon as dishonest. However, there is also a group of activities that would not be necessarily deemed illegal as defined by criminal law, but are included within the definitions used by the participating companies. Examples include serving friends and family while operating a till, claiming points against a loyalty card, hiding stock until it has been reduced in price and then purchasing it, and allowing friends and family to use a staff discount card. While some of these may be permissible as cases of fraud in a court of law, they are for the most part considered breaches of company policies and practices and hence viewed as staff dishonesty. This needs to be borne in mind when reviewing the data in the next section.
Type of staff
Each of the companies taking part use a different nomenclature for the staff they employ: for instance those working on a checkout can be till operators, cashiers or customer assistants. In order to protect the anonymity of those companies that do not wish to be identified, a group of generic titles have been created that cover the primary activities of those included in the data set. These are summarised in the following table:
As can be seen, the vast majority of the data set is made up of staff working at the checkout operating till equipment. The next largest group is staff who have been employed as shop floor staff – restacking shelves and helping customers. The data set also includes a group made up of security officers (4) who had responsibility for guarding the stores (both while the store was open and closed), acting as a visible deterrent, monitoring CCTV, checking staff, and responding to incidents of external shop theft. A similar number of interviews were carried out with staff who worked exclusively in the back-of-store area (when the store was open and closed). Interviews were also carried out with three staff who held management positions, one of whom was a store manager. Finally there were two interviews with staff responsible for the cash office and two for staff who worked in a retail distribution centre as product pickers.
Key Findings
The data in this part of the Report has been organised into four sections. The first will explore the location where the offending took place, the second will focus on the methods used by offenders, while the third will look at the role of process failures in enabling staff to act dishonestly. The final section will look at the views of offenders in terms of how they may have been deterred from committing their offence, or discovered more quickly.
Place of Offending
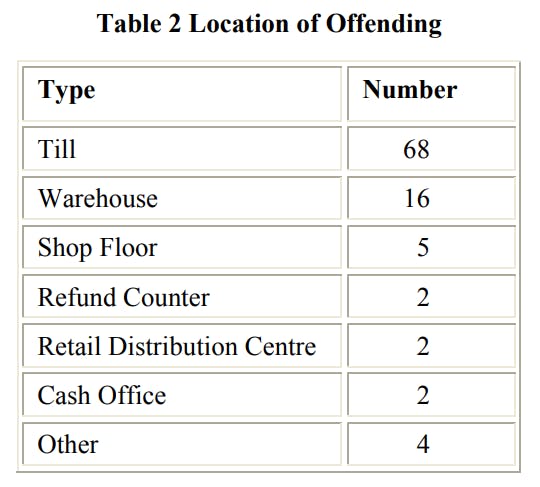
As detailed in the Methodology Section, the 74 cases generated 99 ‘events’ that could be accurately detailed from the interview data. These were carried out at the following locations:
The till was the location where the vast majority of the incidents were carried out – 68 of the 99. This was followed by the back of the store warehouse area (16) and then the shop floor (5). Only a very small number of incidents were perpetrated at the refund counter (2) in the cash office (2) or the retail distribution centre (2). The ‘other’ category included incidents where a security guard had been caught stealing from another retail store, a member of staff was caught erasing CCTV footage and another had been receiving stolen goods. This data fits with current thinking on staff dishonesty – the back room areas and the till offer the best places for staff to offend. For the most part the shop floor was considered too open and well protected, while the cash office was usually protected by CCTV and multiple occupancy procedures. The warehouse area was considered a much easier place to steal stock: ‘there are lots of places where you can hide stuff, eat food, put it in your pockets; not many people around and everybody knows where the cameras are’. Another offender described why the warehouse was a good location for stealing stock: ‘every Sunday morning … no security in, no cleaners in, no managers in … stuff them [cigarettes] on my body … no searches after shift’.
Methods of Offending
Given that 84 of the 99 offending events happened either at the till or in the warehouse area of the store, this section will focus primarily on these two areas.
Offending at the Till
A wide variety of methods were employed at the till to steal stock and cash, or breach company procedures. Detailed in Table 3 are the methods adopted, in rank order of frequency:
The majority of those caught for dishonesty at the till had been stealing cash26. There was relatively little sophistication in the approach they adopted – most simply secreted the cash in their clothing: ‘fold the money compactly in the till and tuck it away in my clothing or shoe’. Others would use the moment when the till was being ‘topped off’ – reducing the amount in the till to within the permissible limit. They would simply take some of the notes and then send the rest to the cash office (via a pneumatic tube system). Another offender was slightly more organised in that they would pass the cash to a family member, pretending that they had got cash back with their bank card or simply give too much change. The cash offenders were interesting for three reasons. First, there was little effort made to disguise what they had done – the till usually would not balance at the end of the trading day: ‘I didn’t try to cover my tracks … just take small amounts and hope that it doesn’t come up’. Secondly, they relied upon multiple usage of the till to try and cover their tracks: ‘there were lots of people using the till in any one shift – how would they know it was me?’ Thirdly, many became progressively greedier as their confidence grew and their offending remained seemingly undiscovered: ‘I started with just a pound or two, and then a fiver [£5.00] and then the odd tenner [£10.00]’. In one of the detailed interviews, an offender gradually admitted to the extent of their cash theft:
‘I never took more than £2 at a time and only once or twice … I was stealing every week … actually it may have been £5 at a time, or may be more … it could be £160, I’m not sure’.
Many relied upon quiet moments in the working day to perpetrate their offending, or they would remove the cash directly after a customer transaction, when the till would be seemingly closed. One offender used the till pin code of another member of staff to cover their tracks, while another was part of a small team (4 people) who all used the same till and the supervisor would log on in the morning and everybody would then use the till: ‘the manager would sign in in the morning and we would use the till under his number and I thought they wouldn’t be able to tell it was me’. On only three occasions did offenders mention using the void option to generate cash in the till for themselves, with the void last item being mentioned twice as the chosen method.
The second most frequent activity at the till was non scanning of items for family, friends and colleagues. This was seen as a very easy option: ‘scanned items through the till and let others go through unscanned although careful to make it look as though items were being scanned’. Doing this for colleagues was mentioned on numerous occasions: ‘lots of staff were doing it for each other – I would do it at least once a week, felt a bit under pressure to do it as she [the other member of staff] can be quite dominating … thought nobody would notice and it [the loss] would be put down to shoplifters’.
As with cash theft, there was relatively little planning involved or attempts to cover their behaviour. Some did mention that they would only do it on the tills that were not covered by CCTV, but on the whole they thought this was a relatively risk-free endeavour. The third most frequent abuse at the till mentioned by respondents was allowing family and friends to use their staff discount card. Most offenders recognised that this was against company procedures but few thought this was much more than a misdemeanour. The fourth most cited activity at the till was serving family and friends. All four companies taking part in this study had an explicit policy that staff were not allowed to do this and if they did, they would be in breach of company policies and liable for disciplinary action. Once again, many staff admitted to doing this but few felt it was anything worthy of more than a minor response from store management. The fifth most frequent activity was misuse of a company loyalty card, primarily to collect points from others’ transactions. This took the form of either covertly collecting points when the till was not being used (such as using the training function to run imaginary items through the till and claim the points) or more overtly when customers did not have a card and were willing to allow the transaction to be credited to the staff member’s card. Either way, it is deemed as fraud by the company and subject to disciplinary action.
The remaining categories in Table 3 were much less frequent activities and were often only committed by one respondent. Stealing phone cards, or topping up mobile phones was relatively rare although quite a few of those staff who said they had stolen cash also said that they would steal phone credits as well. One member of staff admitted to using credit and debit cards accidentally left behind by customers (estimated that she used them to buy goods worth €10,000), while others would steal product vouchers from the till and reuse them when they or their friends and family went shopping.
Offending in the Warehouse
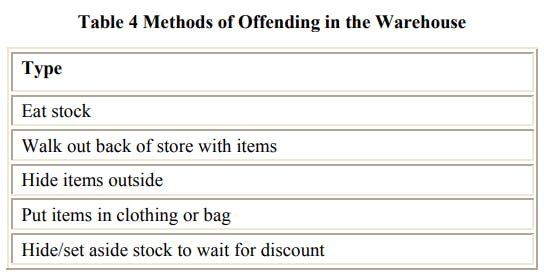
The second most likely place for staff offending to take place was in the back room areas of the store. Table 4 details the most frequent methods adopted by offenders:
The most frequent illicit activity mentioned by respondents was the eating of stock in the backroom areas. All types of staff admitted to doing this. Sweets were the most popular: ‘on the night shift you would always help yourself to crisps and chewing gum’, while another admitted to helping himself to a chocolate bar and sweets that were due for destruction. The same respondent would also part use deodorants and put them back on the shelf! Similarly, the consumption of liquids was also perceived as very common especially by warehouse staff and those working the night shift. The second most common method adopted by respondents to take stock out of the store was to leave with the stock by the back entrance – either quite blatantly in boxes or bags (pretending they have already been purchased) or waiting when the store was quiet and putting the goods in a car or simply walking away. The third method was to hide items outside the store, usually in the recycling or waste disposal unit and then return when the store was closed and retrieve the items. Method number four was to simply put the items in their personal bag or in their pockets and walk out the store as they would normally. The final method identified by two offenders was to purchase items at discounted prices through the manipulation of company procedures. This was achieved through ‘insider’ information on what products were going to be reduced in the near future. Members of staff would put products to one side that they wanted and knew were going to be heavily discounted in the foreseeable future (this was especially the case with post Christmas products when one particular company would discount stock by as much as 90 per cent). Once the discount was available, then the item would be purchased. The store manager in this data set was found to be doing this on a regular basis (he would sometimes hide stock items for many months, or remove items from open sale just before they were due to be discounted). A number of ‘warehouse thieves’ pointed to issues surrounding the security cage and the relative ease with which they could gain access and steal high value items, or the damaged goods area, which was considered equally vulnerable (one member of staff admitted to deliberately damaging stock and then retrieving it from this area). This point will be revisited in the next section.
There was very little evidence of staff stealing to order or selling-on goods to third parties for cash or cash equivalents (such as drugs). Those that did were the exception to the rule in this data set. Most were simply stealing for their own use or for the family and friends. The systematic selection and theft of high value items was not a common theme from this group of offenders – for the most part the thievery was small scale and for personal use only.
Other Areas of Offending
Staff dishonesty in other parts of the store and indeed supply chain were less obvious in this particular data set. Two incidents were recorded in the cash office, and on both occasions, members of staff simply took cash when they were on their own and made no effort to cover their traces – like many of the till operators, they assumed (and hoped) that the discrepancy would be put down to error and no further action would be taken. As mentioned earlier, the shop floor was not seen as an area where staff could easily commit offences – stock was thought too be well protected (through CCTV coverage, tags and staff vigilance). The cases in this data set refer to 5 incidents. The first was staff using their ability to reduce the price of goods for their own benefit (fresh food that was close to sell-by-date). The second was a security operative who found €8 on the floor and pretended to take it to the cash office but in fact kept it for himself. The third was an accusation of a security operative stealing cash from a charity box, while the fourth was the theft of newspapers by one of the night shift. The final incident was a member of staff deliberately damaging an item and taking it to a till and asking for a discount.
The refund counter yielded just two incidents, one when a member of staff colluded with a customer to return an item that had been purchased but the item was not returned (the cash was then shared between them), while the second was slightly more involved and entailed a member of staff generating forged receipts (using a PC and scanner at home) to get refunds. Finally, two incidents were recorded of pickers in a retail distribution centre. Both were using the same methodology. They were colluding with a delivery operative and would over pick and share the proceeds once the vehicle had left the depot.
The Role of Process Failures and Offending
One of the key objectives of this research was to explore the ways in which staff were exploiting existing processes and procedures to facilitate their offending behaviour. What is quite interesting about much of the data is the fact that most staff have to do very little to enable them to carry out their offending. Few make more than a token effort to cover their tracks and the vast majority rely upon the complexity and enormity of the retailing operation to provide a sufficiently foggy picture to reduce the likelihood of detection. For instance, time after time till-based offenders would assume that the sheer volume of customers passing through the till, together with the variety of operatives who would have access to the cash in the till, would mean that their activity would be considered as either simple retail error – an inevitable part of doing business – or impossible to associate with a single individual operator. Clearly given that all 74 respondents in this data set were caught would imply that this is not the case! However, a number of process failures were identified by the respondents:
- Security searches were either not random or simply not done. Many respondents pointed to the inadequacy of the searching policy in their store – ‘I had only one search in four years’. Some said that store managers would ask them to sign that they had been searched when they had not. Another respondent was regularly ‘tipped off’ about when the searches would take place. Few staff saw managers and security guards being searched.
- Staff sharing till pin numbers or not logging off at the end of shifts. The use of unique identifiers at the till is a vital component in creating accountability at the checkout. Numerous staff identified irregularities in this process including multiple use of a single code or staff logging in as another employee.
- Tills not being emptied and checked on a regular basis. Many staff pointed to the apparent camouflage multiple use of the same till provided, particularly when cash was not checked and reconciled frequently.
- Staff not leaving by staff exits. As the data shows, theft of stock was often achieved through offenders leaving through the back of the store avoiding the normal checks put in place for them. Examples were also provided of staff leaving through the customer exists as well.
- Irregularities in use of the security cage. Many examples were provided of the security cage not being locked when not in use, or staff not signing the appropriate documentation when they took the key to gain access to it.
- Unauthorised staff entering the warehouse. For some retailers, only certain types of staff are allowed in the back room areas. Respondents gave examples of where this procedure was not being followed.
- Lack of supervision of night shifts. Few managers like working anti-social hours and a number of respondents highlighted the enhanced opportunities for eating and stealing stock at night when supervision was at best minimal.
Offending and Prevention
The final section collects together the thoughts of respondents on what would have either prevented them from offending in the first place, or would have meant that they would have been caught much quicker. A number of themes emerged. First, staff gave a resounding vote of confidence to the use of CCTV. A number of till-based offenders stated that they would only offend on the tills that were not covered by CCTV. This is interesting because most staff would know that it is rarely monitored constantly, indeed some complained that security operatives were not doing their job properly because they should have been watching the CCTV monitors more. However, on the whole staff were not concerned about being caught in the act by CCTV (although some did say this) – they were much more worried about their theft of cash ‘event’, and the inevitable ensuing till discrepancy, being accurately tracked back to them. It is the evidential nature of CCTV and its ability to generate accountability for losses at the till that made them highly wary of offending within its gaze. Hence many respondents said that cameras should be placed over every till. This is interesting because numerous technologies are coming on to the market that can begin to combine till activities with visual images. Staff offenders themselves suggest that this might be a powerful tool in combating dishonesty. Similarly, offenders in the warehouse areas suggested that more cameras would make them more cautious and less inclined to steal or eat produce. The difficulty for many back room areas is reducing the number of blind spots that can be exploited by offenders.
Secondly, respondents thought that the use of searches should be reinforced, particularly in terms of the range of staff covered and the randomness of the event. Too often staff felt extremely comfortable walking out of the store assured in the knowledge that they would not be searched. The view was that a greater degree of deterrence would be achieved if staff thought there might be a realistic possibility of them being searched.
Thirdly, staff wanted to see better training on how to use the till and greater awareness of the potential it offered to provide data to management on deviant behaviour. Few offenders at the till understood the implications of their actions and the likelihood that reports were generated that linked transactional data to individual members of staff. Their degree of naivety in the way that they crassly stole cash from the till speaks volumes about their ignorance relating to data matching and exception reporting. Creating a fear factor together with a sense of inevitability that deviant till behaviour will be discovered was seen as a key approach in reducing future offending. Similarly, some staff suggested that the level and frequency of till checks should be increased while others thought that checking the balance of the till after each operator would increase the likelihood of detection and hence make staff more cautious. This has clearly got its merits in terms of generating transparency and accountability at the till, but may have severe cost implications were it to be carried out in a large retail environment.
Fourthly, some staff thought that there should be better screening of staff to ensure that those who had offended previously were not allowed to work in a retail environment again. This is certainly an idea that has been mooted previously and a similar scheme is currently being used in the US27. In Europe, concerns about data protection and human rights would need to be resolved before such as scheme could be introduced.
Fifthly, there was concern that not enough was done to make sure staff were fully aware of the implications of breaching company procedures relating to staff discounts and loyalty cards. Certainly this type of ‘offence’ was very prevalent in the current data set and often staff claimed that they were not aware that they could not do this. It was suggested that more could be done to ‘advertise’ this fact amongst staff.
The final point mentioned by staff was the importance of security operatives and supervisors making regular checks and patrols throughout the store. This was seen as a way of keeping staff on their ‘toes’ and reducing the opportunity for deviant behaviour to take place unnoticed. Certainly, much of the work of security staff is often focused on the risk of external theft, particularly in terms of shoplifters, and there may be a case that this balance needs to be readdressed to incorporate concerns about staff theft as well.
Conclusions
In many respects this has been a highly instructive study. Not least because prior to this few if any researchers had attempted to speak directly to retail employee offenders about their activities – all previous analysis had been based solely upon talking to retail staff in general, or security staff employed to catch them, or analysis of company records on who had been caught and what they had stolen. The voice of the offender was largely silent. What was also missing was an appreciation of how they went about their offending – where were the places that they carried out their deviant behaviour and how did they do it? This study has attempted to address this deficit.
A number of themes have emerged from the data collected as part of this study. First is the relative simplicity of the offending that takes place – for the most part there is little forward planning nor development of intricate schemes to cover tracks – offenders simply take cash and stock and hope they will not get caught. They primarily rely upon the monolithic nature of modern retailing with its vast product ranges, huge economies of scale and multitudes of employees, to cover their deviant tracks. Their rationale for offending is based primarily upon opportunity, hope and lack of transparency. The staff in this data set generally perceived it to be easy to commit dishonesty – the fact that they were all caught means very little in these circumstances – the perception was there that they could do it and get away with it (which for some they did for a considerable period of time). Ensuring that retail staff have a mindset which says that it is difficult to be dishonest and that if they are, they are highly likely to be caught, is an important message that needs to be conveyed more robustly.
Secondly, the till was seen to be the most vulnerable point in the retail store – something which had been speculated about by shrinkage practitioners for a considerable period of time. There was little evidence of staff (other than some exceptional cases) stealing large quantities of stock from the back of the store – most seemed to be consuming stock or stealing for personal use. The till was the point at which staff could steal cash, cash equivalents (phone cards, vouchers, gift cards, loyalty points and discounts) and give stock away to family, friends and colleagues. It was the gateway to rich pastures of opportunity. Once again, despite the universal use amongst all participating retailers of unique till personal identification numbers, staff felt that they had sufficient anonymity to carry out quite brazen acts of theft of cash. Key to their thinking was the multiple use of the same till by many members of staff (creating uncertainty about responsibility) and their naivety in not appreciating the recording and monitoring capability of modern EPOS systems. They also felt reassured by a company culture that was inclined to put losses in the store down to external thieves – the loss of stock was due to the local drug taking youths and the prioritisation of this problem by store security staff offered reassurance to offenders.
Thirdly, the importance of surveillance was also a key finding from this study – both its absence and its potential, and the form it could take. For till-based thieves, the presence of a CCTV camera that could monitor their activity was seen as a real deterrent. They were less concerned about being caught in the act but more worried about the eventual till discrepancy triggering an investigation that would ultimately review CCTV footage which would in turn provide evidence of their wrongdoing. This for staff was the real power of the CCTV system. To a lesser extent, staff offenders in the back room areas also pointed to the deterrent potential of CCTV and the impact its presence had upon their behaviour. They were much more likely to try and find places where they would be out of its ‘gaze’ to commit their offending. But it was not just CCTV that was seen as an important form of surveillance, staff were also clear that one of the roles of supervisors and managers should be to ‘patrol’ the store to make sure that staff were not engaged in deviant behaviour, particularly in the back room areas.
Fourthly, the role of checks and balances within the overall operating procedures of the store is clearly a key factor in influencing offending by staff. The operation of the till has been revolutionised in the past 10 years, not only in terms of Electronic Point of Sale (EPOS) scanning but also in the plethora of functionality now available to staff operating them. Activities that were traditionally possible only at a specialist point within the store or were only carried out by senior staff, such as refunds, voids, discounts and multiple purchases, can now be done by staff who may have been working for the company for only a few days. Obviously this has been driven by a demand to improve the customer experience, primarily through reducing waiting times at the checkout, but it has undoubtedly added an increased risk to the integrity of the store. Like many areas of retailing and security, there is a delicate balance to be struck between maximising sales and minimising the likelihood of loss. There is an argument that increased till-operator discretion covering key transactional activities that current till configurations offer, is tipping the balance too far towards security risk. It may be the case that companies need to reflect carefully upon what access and privileges they actually want to give to till operators and whether a greater degree of oversight is required in order to ensure that abuses at the till do not take place (or at least are perceived by staff to be highly risky and likely to lead to their detection).
Fifthly, an area that has been rather unfashionable in recent years within the world of retail security management appeared as a recurring theme in this research – staff searching. The drive for ever increasingly sophisticated technological solutions has dominated the retail loss prevention agenda for a considerable period of time, not least because ‘solution’ providers are keen to sell their new innovations to retailers looking for the ever illusive technological panacea. Respondents to this study reflected many times upon the deterrent impact a properly managed staff searching scheme would have, particularly relating to the theft of goods. They flagged up the usual problems with such schemes – lack of randomness, inability to search certain parts of the body and lack of consistency across all types of staff, but they were clear that a well managed staff searching policy would undoubtedly have deterred many of them from trying to carry goods out of the store.
Sixthly, the importance of staff integrity emerged as an important theme, particularly relating to how a significant number of the offenders were caught. Other members of staff actually telling either managers or security personnel that they had witnessed dishonesty or were deeply suspicious of another member of staff was an important mechanism in identifying deviant staff members. It is worth reflecting that the vast majority of staff are largely honest and consider dishonesty as morally wrong and not something they are willing to tolerate in their workplace. The idea that stock losses attributed to store staff puts everybody under suspicion does not rest easily with many workers and they are far more likely to want to ‘clear their name’ through exposing those who are carrying out the dishonesty. It could also be the case that staff do not want to work with known thieves because it could put their own personal items at risk of theft as well. Either way, tapping into this resource could be an important mechanism for companies to consider in their overall strategy to reduce staff dishonesty.
Finally, the issue of non-scanning of goods at the till was a key method adopted by some staff to steal goods for their family, friends and colleagues. For the two security specialists taking part in this study, and indeed many other loss prevention practitioners who had been interviewed by the author in the past, this would undoubtedly be the way in which they would steal if they were so inclined. It was seen as a relatively risk free enterprise because of the ability to hide non scanned items amongst legitimately purchased items and the lack of any obvious direct link between the goods stolen and the activity at the till (upon discovery, possibly many weeks later, it would be assumed that the goods had been stolen by shoplifters). As one senior loss prevention practitioner put it: ‘coming up with a solution to sweethearting is currently the holy grail of loss prevention’28. As yet, few realistic options have been developed that would cover most items stocked by large retailers, although developments in digital CCTV technologies may begin to offer some interesting avenues of exploration.
Recommendations
This project has attempted to shed light on a problem that has vexed loss prevention experts for many years. It sought to add a new dimension to our understanding of staff dishonesty through listening to the accounts and experiences of the offenders themselves. From this work, a number of recommendations can be made about how organisations may want to think about this problem in the future, and more importantly, develop strategies and approaches more likely to reduce its prevalence.
Developing a Data Mining Capability at the Till
The vast majority of those caught offending at the till were completely unaware of the data gathering and exception reporting capacities that modern EPOS-based till operations can provide. They thought that their particular incidents of offending would be lost in the sea of transactions and interchanges of operators that now makes up the modern retail environment. Having the capacity to quickly identify unusual or deviant behaviour through some form of exception reporting or transactional monitoring system seems a vital tool for loss prevention practitioners. There are a number of issues within this:
- Companies need to develop a regular investigative process that ensures all till irregularities are analysed.
- Store management is given the capacity to access the data mining function to enable them to monitor their staff.
- The data mining capability needs to be regularly advertised to store staff to ensure that new staff are made aware of its potential to identify deviant behaviour, and existing staff are reminded of it functionality. For the latter, this may require the publicising of recent investigations where staff have been dismissed through the use of data mining.
- Companies need to develop a list of the key till deviance indicators that will alert store management and the loss prevention team to likely deviant behaviour, such as the number of last item till voids, till draw opening behaviour, unusual sales of phone top-up cards and so on. They must also decide upon the tolerance levels for each of the deviancy indicators that they develop to enable effective exception reporting to take place. Store management will not want to be dealing constantly with too many false positives.
ECR Europe is about to start work on a project assessing the ROI on a range of technologies, including data mining, which will report in late 2007. The evidence to date from this project would suggest that its absolute value in detecting and deterring staff dishonesty seems very clear and apparent. Work is also underway to identify the most common ‘scams’ or methods used by offenders, which will shed further light on the sorts of areas of behaviour that need to be monitored and measured by retail companies.
Staff Monitoring and Surveillance
A clear message came from the dismissed employees who contributed to this project – if processes for regular checking by senior staff are developed and or adhered too, and an evidential link (primarily through the use of CCTV footage) can be made between themselves and store losses, then they are highly likely to desist from committing deviant behaviour. More specifically:
- The use of staff searching seems to offer an important deterrence capability, but only if they are genuinely random, frequent and implemented across all levels of staff.
- Staff working when the store is closed (night shift shelf replenishers, cleaners etc) need to have adequate levels of management supervision. The opportunities for the consumption and theft of stock is significantly enhanced for these groups and measures need to be taken to increase their likelihood of detection.
- The use of CCTV, especially at the till could have a dramatic impact upon levels of offending at this location. The key to its success is not necessarily catching members of staff in the act of stealing, but providing a link between a till-based discrepancy and a member of staff – its role is one of generating transparency and accountability rather than acting as direct thief catcher. Similarly, staff offenders in backroom areas were also highly apprehensive of being dishonest within the gaze of CCTV cameras although their opportunities for re-locating their offending were more abundant than their till-based colleagues.
- The extent to which till operators are given discretion to carry out a range of potentially risky transactional procedures (such as voiding, price reductions, using discount cards, etc) without any form of managerial oversight needs to be carefully considered. There is a clear balance to be struck between achieving high levels of customer satisfaction at the till and minimising store exposure to staff dishonesty. Companies need to have a careful review of what staff should be entitled to do without some form of oversight from store management.
Regular Reviews of Key Vulnerable Processes
Throughout the data collected for this research, dishonest staff highlighted the relative ease with which they could carry out their behaviour, but they also pinpointed a number of procedures that were prone to failure through lack of adherence and monitoring, which facilitated their thieving. Three particular areas related to store deliveries, the use of the security cage and areas set aside for damaged or returning goods. All retail companies have well established procedures for each of these areas but the research identified a lack of transparency and adherence in the way that staff worked. Companies should therefore encourage store management to carry out regular reviews of the key vulnerable processes within their stores and answer a series of simple questions:
- Are staff following the procedures?
- Is there proper transparency and accountability for any actions undertaken by staff relating to these vulnerable activities?
- Are staff being properly supervised in these areas?
- Is there evidence of unauthorised staff in these areas?
By doing this, store management will be sending out an important message to the staff working in these areas (it could be that security staff in the store also patrol these areas as well as the front areas of the store).
Hot Product Reviews
The rasion d’etre of the security cage in a retail store is to reduce the vulnerability of particular products that have been previously identified as at risk to theft by staff. As the previous recommendation noted, strict adherence to the procedures relating to this space is vitally important if losses are to be minimised. However, protection of one group of products may displace offending to other types of less protected product, and there is some evidence from this research that this may be taking place. It is important therefore that store management together with the loss prevention team regularly review which products are currently vulnerable to loss within a given location. This, where possible, should be based upon staff dishonesty-based data rather than more generalised data referring to losses caused by customers and staff.
Staff Awareness Programmes
The extent to which staff naivety played a role in ‘explaining’ their deviant behaviour and ultimately in their apprehension was extremely profound in the data set analysed for this research. Most staff who were caught being dishonest at the till simply did not realise that their actions were likely to come to the attention of store staff, or that if it did, then it would not be possible to link it to them in particular. This draws attention to the need to raise considerably the awareness of staff about the security capabilities relating to staff dishonesty within the organisation. This should be done in three areas:
- The analytical capabilities of the company. Staff need to be regularly made aware that their activities at the till are closely monitored and analysed. It should be made clear upon induction and at regularly intervals throughout their employment with the company. It should also be reinforced through the publicising of incidents of staff dishonesty that have been identified through this approach.
- The surveillance capability of the company. Most retail organisations are now investing routinely in CCTV technology and the evidence from this study would suggest that its deployment at the till can have a strong deterrent impact. Staff need to be made aware of its capability, again at induction and routinely whilst they are working. This could be done through regular visits to the CCTV room, mobile CCTV monitoring systems or through the publicising of cases where staff have been caught through its use. Either way, their suspicions about its capability need to be routinely reinforced.
- Awareness of the consequences of offending need to be brought to the attention of all staff. The taped interviews with offenders was particularly enlightening on this point and showed the lack of awareness of the consequences of their actions. Few thought that they might lose their jobs and even fewer thought the police would be involved. The realisation that the police had been called and that they were to be taken through the store and out the customer exit was something that filled most offenders with absolute horror. All staff need to be reminded of the company policy on dealing with those suspected of behaving dishonestly. In this respect, the company policy needs to be robust, uncompromising and consistent across all grades of staff – any deviation from this is likely to send a message to store staff that the company tolerates such behaviour. Once again, it is a message that needs to be reiterated throughout the employment history of staff.
Keeping staff awareness high on any issue relating to shrinkage and stock loss is challenging – priorities change and enthusiasm wanes. Store management teams and loss prevention departments need to constantly be thinking about new ways of getting the message across while not forgetting that with relatively high levels of staff turnover, the old message may not be that old.
Management Performance Reviews
As other research on staff dishonesty has shown the attitude and behaviour of store management can have a profound effect upon the way in which their staff perceive the acceptability or not of certain practices. Example setting is an important function of management. Therefore, store management should be regularly reviewed on their own adherence to procedures and their attitude towards following company guidelines. They need to be reminded of their impact as role model within the store on the staff that work under their influence. In addition, managers also need to take full responsibility for ensuring that any security staff employed in the store, are also following all the company policies and procedures. It is easy for such staff to see themselves as above suspicion and store management need to recognise that they could potentially be a greater threat to security than any other staff working in the store.
Developing a Culture of Intolerance
Recognising that most staff are inherently honest, particularly when they are presented with few opportunities for ‘risk-free’ offending, is an important message to take away from this report. Indeed, developing a culture of intolerance of dishonesty could be the most productive strategy any company could adopt. Few generally honest people are keen to work in an environment where they are likely to be tarnished with the suspicion of dishonesty due to the actions of others. They would much prefer to have the thieves exposed and their reputation remain unsullied. There is plenty of evidence from this study that staff are willing to ‘blow the whistle’ on other members of staff who are being dishonest and so it may be important for companies to reflect upon how such a culture can be encouraged, and how staff can be facilitated in their efforts to alert the company to deviant behaviour. In the past this has been achieved through anonymous phone lines, suggestion boxes and indeed reward schemes. Whatever approach is adopted, getting staff to play an active role in the policing of their own work space could be a cheap and effective way of minimising a companies exposure to staff dishonesty.
Main office
ECR Community a.s.b.l
Upcoming Meetings
Join Our Mailing List
Subscribe© 2023 ECR Retails Loss. All Rights Reserved|Privacy Policy